others-prepare for cks exam with me 8: Security context in Kubernetes
1. Purpose
In this post, I would continue to write about preparing for the CKS (Certified Kubernetes Security Specialist) exam. I would write my own notes about the exam, and you can refer to these articles to prepare your own.
List of the series of posts:
-prepare for cks exam with me 1: Linux user and group management
-prepare for cks exam with me 2: Linux ssh hardening
-prepare for cks exam with me 3: Linux remove obsolete packages and services
-prepare for cks exam with me 4: Linux kernal hardening
-prepare for cks exam with me 5: Linux UFW(Uncomplicated firewall)
-prepare for cks exam with me 6: Seccomp in Linux, Docker and Kubernetes
-prepare for cks exam with me 7: Apparmor in Linux, Docker and Kubernetes
-prepare for cks exam with me 8: Security context in Kubernetes
-prepare for cks exam with me 9: Admission controllers in Kubernetes
-prepare for cks exam with me 10: Pod security policy in Kubernetes
-prepare for cks exam with me 11: Open policy agent in Kubernetes
-prepare for cks exam with me 12: Secrets in Kubernetes
-prepare for cks exam with me 13: Container runtimes(gvisor/kata containers) in Kubernetes
-prepare for cks exam with me 14: Container Image security in Docker and Kubernetes
-prepare for cks exam with me 15: How to print docker images of all pods in kubernetes
2. Environment
- CKS
- Ubuntu System
3. Security context in Kubernetes
3.1 What is security context?
A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to:
- Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID).
- Security Enhanced Linux (SELinux): Objects are assigned security labels.
- Running as privileged or unprivileged.
- Linux Capabilities: Give a process some privileges, but not all the privileges of the root user.
- AppArmor: Use program profiles to restrict the capabilities of individual programs.
- Seccomp: Filter a process’s system calls.
- AllowPrivilegeEscalation: Controls whether a process can gain more privileges than its parent process. This bool directly controls whether the
no_new_privsflag gets set on the container process. AllowPrivilegeEscalation is true always when the container is: 1) run as Privileged OR 2) hasCAP_SYS_ADMIN. - readOnlyRootFilesystem: Mounts the container’s root filesystem as read-only.
3.2 Set securitycontext for pod and containers
Security context can be applied to kubernetes pod and(or) containers, such as follows:
apiVersion: v1
kind: Pod
metadata:
name: security-context-demo
spec:
securityContext:
runAsUser: 1000
runAsGroup: 3000
fsGroup: 2000
volumes:
- name: sec-ctx-vol
emptyDir: {}
containers:
- name: sec-ctx-demo
image: busybox
command: [ "sh", "-c", "sleep 1h" ]
volumeMounts:
- name: sec-ctx-vol
mountPath: /data/demo
securityContext:
allowPrivilegeEscalation: false
The security context for pod:
securityContext:
runAsUser: 1000
runAsGroup: 3000
fsGroup: 2000
The security context for container:
securityContext:
allowPrivilegeEscalation: false
If the security context is defined in both the pod and the container, then the container’s configuration would override the pod’s , just like the object-oriented programming.
Security settings that you specify for a Container apply only to the individual Container, and they override settings made at the Pod level when there is overlap.
Just as the following picture shows:
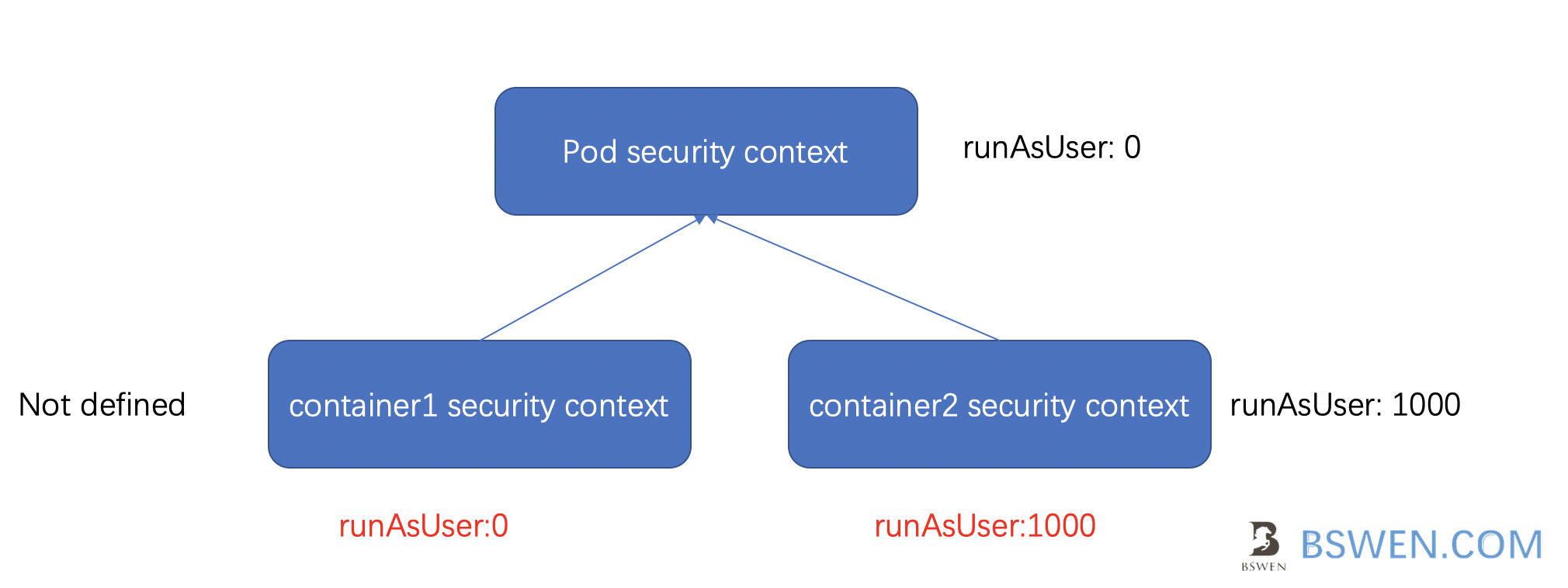
-
The pod security context defines the runAsUser=0
-
The pod has two containers: container1 and containter2
- container1 does not define security context, so it inherits the settings from the pod
- container2 defines the runAsUser security context that is conflict with the pod’s security context settings, then it would override the pod’s settings, the actual value of runAsUser is 1000.
The above bullets are not a complete set of security context settings – please see SecurityContext for a comprehensive list.
4. Summary
In this post, I write some examples about security context in kubernetes.